Secure Access
Maximum Protection for Your Digital Communications
Secure Access is anti-wiretapping encrypted communication software that supports audio calls, video calls, chatting, and SMS. The system is built on two main infrastructures—the internet and GSM networks with cryptographic limits that ensure comprehensive security. Secure Access uses password-based authentication and runs on Android mobile devices without being limited to specific types or brands of GSM devices.

Configuration
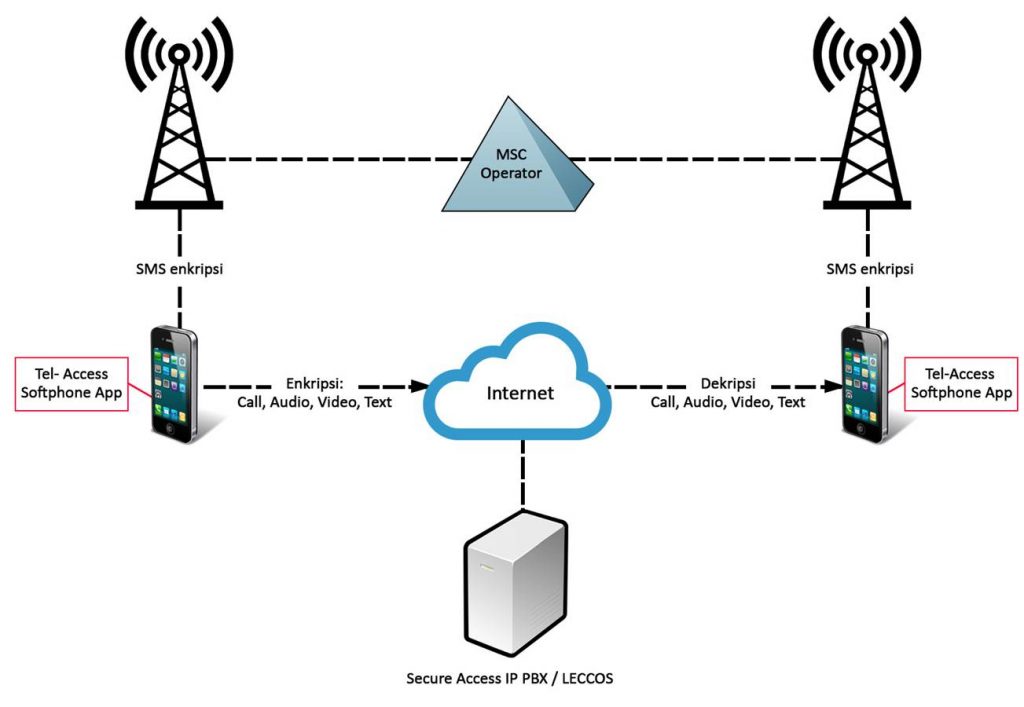
Input from one application to another via the SIP Server, so that applications do not communicate directly point-to-point but via the SIP Server. The purpose of this is for the SIP Server to record the last IP of each application for mutual communication.
For SMS communication, the output from the application is encrypted as an SMS and then transmitted via the GSM frequency medium. Another application on the operator’s side uses the GSM frequency in the form of SMS data, which is then encrypted. The Secure Access application decrypts this data so it can be read by the receiver.
Protocol

Audio Call
Service call audio is encrypted using the SRTP (Secure Realtime Transport Protocol) protocol with G729 audio codec and TLS (Transport Layer Security) SIP Signaling.

Video Call
Video calling service using the SRTP (Secure Realtime Transport Protocol) audio protocol and VP8 video codec, G729 audio codec, and TLS SIP Signaling

Chat
The TLS Protocol chat service uses SIP Signaling and the DH (Diffie-Hellman) protocol for each conversation, which is encrypted with AES 256 (Advanced Encryption Standard).

SMS
The SMS service enables data transfer between devices via SMS messages sent with random passwords that cannot be read without Secure Access Software. Each conversation uses the Diffie-Hellman protocol and is layered with AES (Advanced Encryption Standard).
Encrypted calls from your current phone
Make and receive fully encrypted voice calls on your mobile device. All you need is a data connection (EDGE, 3G, LTE, or WiFi). Every call you make is secured using a new set of unique keys, with advanced MiTM (Man-in-the-middle) attack detection to prevent third parties from eavesdropping on your calls.
Steps to protect your calls and SMS
Making calls and sending text messages
Enter a number or select a contact from your address book. The secure access app works like a regular phone with access to all your contacts and complete call history. With a secure access subscription, you can make encrypted voice calls to other secure access users. For SMS, you can write messages to anyone without being intercepted. With a secure access subscription, you can create encrypted text messages to other secure access users.
Secure access network
Our secure network decides how to connect your call. Our secure core network is purpose-built to provide secure voice services to millions of global users. Our scalable platform runs on sophisticated hardware with full redundancy built in.
Unique keys
Each call has a different set of keys, so even if an attacker finds the key, it will be useless for your next call. Each call uses a unique set of 2048-bit encryption keys, which are securely agreed upon between the two devices. Only you and the person you are calling know these keys, and they are destroyed when you end the call.
Your call is now encrypted
Your conversations are now encrypted in real time. Your calls cannot be tapped, recorded, or intercepted. AES 256-bit encryption: every call is encrypted on your device, and only the other party in your call can decrypt it. Third parties attempting to listen in or record your calls will only hear random noise.
Secure hybrid calls to any phone
Your calls to any number worldwide are fully encrypted between your device and the Secure Access network. This protects your calls when you travel abroad or use untrusted Wi-Fi or mobile data connections, while allowing the flexibility of a regular cell phone to call any number. We call this technology Hybrid Secure.
Based on what has been agreed upon security standards
All your calls are encrypted using AES-256 (Advanced Encryption Standard) cryptography. A strong, unique 2048-bit key used for each call is generated between Secure Access devices using the Diffie-Hellman key agreement protocol, which provides Perfect Forward Secrecy.
Secure Access Network:
A network you can trust
All your calls are encrypted using AES-256 (Advanced Encryption Standard) cryptography. A strong, unique 2048-bit key used for each call is generated between Secure Access devices using the Diffie-Hellman key agreement protocol, which provides Perfect Forward Secrecy.
